SMEs are also targeted by cybercriminals.
Over the past two years, there have been quite a few reports of companies whose websites were “taken down” by cybercriminals.
Only after paying hefty sums of money was the company in question accessible to its customers again.
Recently a chain of dental practices and in the spring Artis in Amsterdam.
In both cases, the impact was enormous.
Business is completely disrupted at such times.
“My company is too small to make anything”
Many business owners will think this and, as a result, things can actually go wrong.
Cybercriminals look for the path of least resistance and only then look for possible gains.
Even if the ransom in the case of ransomeware is not so bad and you are back on the air quickly, you still have to wonder what will be done with the customer information stored in the website’s database.
Security is more important than a low monthly fee for hosting
SME entrepreneurs often make a reasonable investment in developing a good Web site.
Only too often they choose cheap hosting to keep the recurring monthly costs low.
A good example of how cheap turns out to be expensive.
What are the key security issues in hosting?
When it comes to (WordPress) website security, there are several things that need to be properly taken care of:
- Secure updates to templates, plug-ins and WordPress core itself;
- Regular server-level malware scans;
- A software- and hardware-based firewall;
- Additional DDoS protection;
- Use of the latest PHP version (HardenedPHP);
- Regular external backups.
At the bottom of this blog you can read what this point by point means
But surely every hosting provider offers this?
If only that were true.
You would think it would go without saying that all hosting companies offer this by default.
Unfortunately, this is not so!
The reason hosting companies don’t take these actions is:
- It takes more resources (and therefore money) to set up and maintain malware scans, backup servers and routines;
- Additional backups also require additional server space that they prefer to sell to hosting customers.
- Tailoring firewall/modsecurity specifically to individual websites takes more time
- Not every hosting company specializes in WordPress
In addition, some of the work is offered as an option or left out of the subscription so that hosting can be offered inexpensively.
Managed WordPress Hosting offers a solution
So both end users and Web site developers have a lot on their plate when it comes to security.
For the former it comes at the expense of doing business and for the designer at the expense of his or her creativity.
For exactly that reason, in 2015 we started offering Managed WordPress hosting.
Offering as a full-service service all the things that we ourselves as developers had been running into since 2009, but wanted to get right for my clients.
Always personal contact!
So WP Provider was born out of personal need for ultimate hosting and personal contact when it matters.
By and for WordPress enthusiasts.
And the latter remains manageable by offering this service only through web designers.
We focus 100% on the hosting and the designer on the design for his client.
If you have any questions about this.
Feel free to give us a call to discuss the possibilities.
Marco Kroon
__________________________________________________________
For the foodies…
As promised, below is another explanation of the six key points for a secure Web site:
Malware Scans Malware stands for “malicious software” It is an extended term for malicious code that hackers use to gain unauthorized access or do damage to your WordPress website.
In most cases, a bot or hacker will exploit a security vulnerability.
If a plugin is no longer supported by its developers and thus no updates are released for it, it is important to take active action on it.
You definitely want to prevent your website from being given an SEO penalty by Google, which is why we perform several scans at the server level including our WP eXploit scanner tool that actively scans files as they are uploaded to the server through FTP or via WordPress directly, for example.
It can detect suspicious files on the server and prevent most (with the exception of zero-days (the unknown exploits) from being uploaded or executed on the server. Software & hardware based firewall Through our firewall solution, unused ports are closed, access to certain services is protected and logs are continuously scanned for suspicious activity such as a suspicious number of login attempts to WordPress or the email boxes.
IP addresses and ranges are blacklisted so that the attack is stopped.
It recognizes many different attacks such as port scans, SYN floods and brute-force attacks.
DDoS protection
If a Ddos attack is involved, sometimes this is not enough and the Ddos protection shield is enabled.
Our proactive, real-time monitoring capabilities effectively detect and eliminate high-volume attacks.
When we encounter a DDoS attack, DDoS Shield separates clean traffic while the attack is redirected to our DDoS scrub center.
We also have Modsecurity active by default for your account which ensures that suspicious requests are filtered out immediately.
Security headers
HTTP security headers are, in my opinion, a fundamental part of website security.
By enabling appropriate headers at the server or application level (WordPress), you can improve the CMS’s resilience against common attacks, including cross-site scripting (XSS) and clickjacking.
When a user visits a site through their browser, the server responds with HTTP Response Headers.
These headers tell the browser how to behave while communicating with the site.
By applying the right security headers, you are taking a good step toward a more secure Web site.
Hardened PHP
WordPress recommends that the latest PHP version always be used (and so do we).
Of course, this is not possible in practice because, for example, custom plug-ins are written for an older PHP version or because plug-in developers have not yet rewritten their plug-ins for the latest PHP version.
If an update of the PHP version is performed, the worst case scenario is that a fatal error occurs and the website can no longer be reached.
For this reason, we use HardenedPHP, a way to continue using older PHP versions without compromising security.
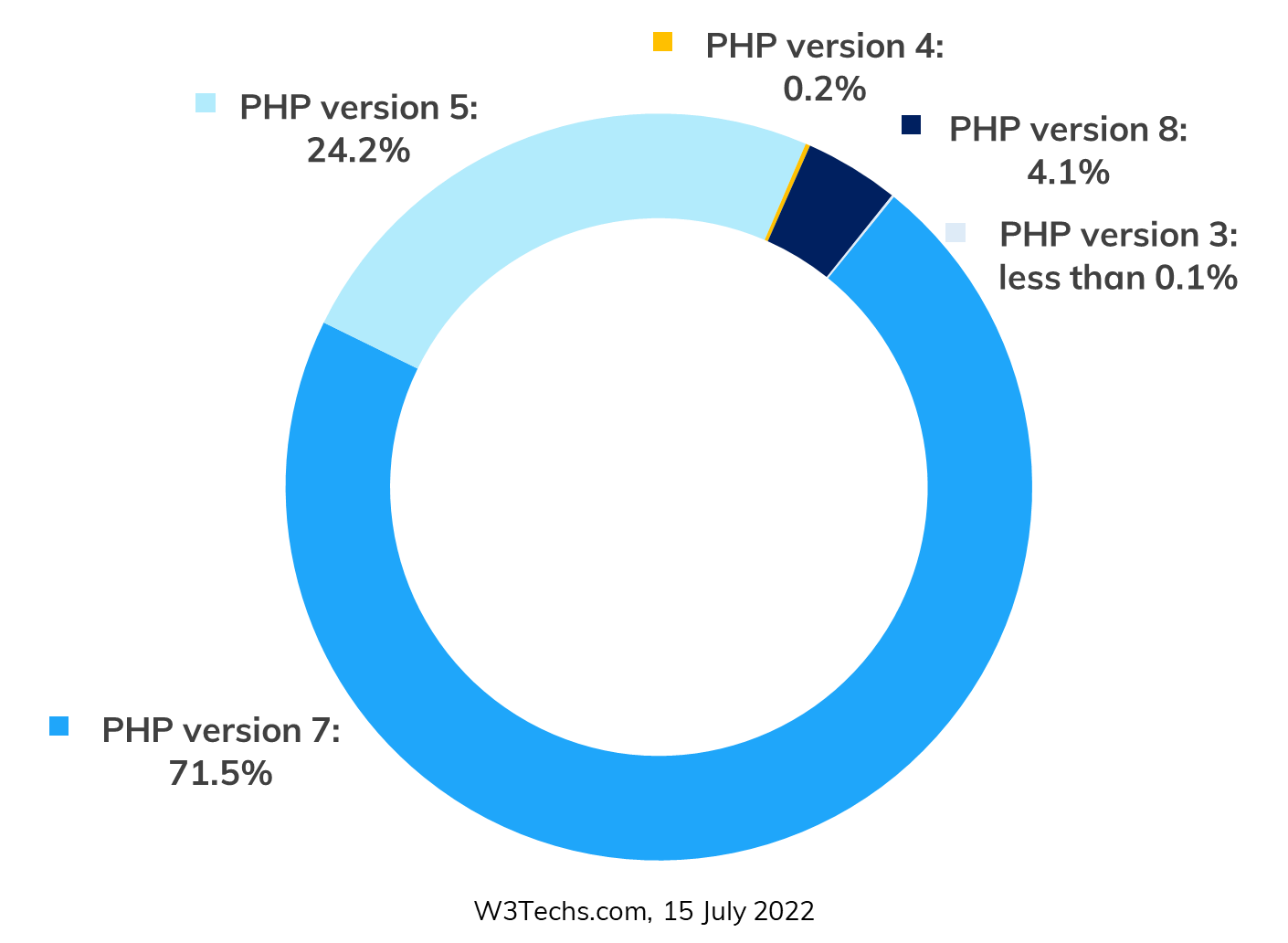
Very popular versions of PHP, used in nearly 85% of all PHP sites, are no longer supported by the PHP.net community.
HardenedPHP secures old and unsupported versions of PHP – 4.4.9, 5.1, 5.2, 5.3, 5.4, 5.5, 5.6, 7.0, 7.1, 7.2.
HardenedPHP secures old, and unsupported versions of PHP.
In those old versions, including the widely used 7.2, 7.1, 7.0 and 5.6, vulnerabilities, even if discovered, are not patched by the PHP.net community.
HardenedPHP takes care of all this.
PHP represents more than 79.2% of all server-side scripts.
Because of this wide application usage, PHP is constantly being exploited by hackers, leaving sites vulnerable.
HardenedPHP keeps your clients and servers safe by patching all PHP versions against known vulnerabilities – even those versions not supported by the PHP.net community.
More than 100 vulnerabilities, many of which were critical, have been discovered for unsupported versions of PHP.
All of them have been patched by CloudLinux.
Backups
If something does happen don’t be alarmed, we can restore a backup for you immediately.
In addition to total snapshots of all servers on the platform (against ransomware), backups are also made of the WordPress installations.
Because we advocate backups of backups, these are also additionally backed up off-site in another data center.
What if something does happen?
By default, we make daily backups of your WordPress website.
In the worst case, we can go back in time to when the website was fully functional.
What if something happens to the backups? We’ve thought of that, too.
Always make backups of your backups.
In addition to full snapshots, we also export our backups off-site to another secure location in another data center.
Keep moving
“Securing a Web site is like riding a bicycle. To keep your balance, you have to keep moving.” This is how Albert Einstein’s famous bicycle quote would have looked if he had been a cyber security professional. Fortunately (or not) he wasn’t. But to keep the analogy with the bicycle: you can’t stop pedaling. The moment you do, the bike slows down and you just end up falling over. And that’s exactly what we want to avoid. But when it comes to cycling, not all pedal strokes are the same. Some are smooth, some are hard, some make you cover shorter distances, while others take you longer.